A few weeks ago, someone shared a story about a man who lost his entire life savings – over $1 million – because his accounts were hacked.
In California, a student used a similar trick to steal $7.5 million in Bitcoins from an unsuspecting victim. This criminal was brought to justice and is serving time, but the method he exploited is still around – and growing in popularity.
Even though these crimes carry up to a 20-year jail sentence, the opportunity to steal millions of dollars from behind a computer will no-doubt spark more criminals to try.

The method I’m referring to is called a “SIM-Swap”. This works by having someone effectively steal your phone number long enough to bypass your security methods and get access to your most secure accounts.
A SIM-Swap works like this:
1. Identification: Someone identifies you as a target of something the thief wants. Maybe you have a great handle on a social media site, you’ve mentioned somewhere that you have a bunch of money or you’ve decided to share your entire net worth on your blog.
2. Research: The thief does their homework on you, learning as much as they can. SSN, mothers maiden name – anything they can dig up on the dark web through various data breaches. The important things are your primary email address, your phone number, and wherever they want to steal is located. They might even stalk you on social media and find a time to continue on to step 3 while you’re on vacation.
3. SIM-Swap: The thief calls up your cell phone carrier provider pretending to be you. They give a sob story about how you lost your phone and need the number ported over to a new phone. At this moment your phone with the original number will begin to show “no service”. This is a tip that your phone has been SIM-swapped. If the thief chose a time you were traveling then you might not immediately realize what’s happening.
4. Getting Access: Now that the thief has your phone number and some data about you, things get easier (for them that is. Things get harder for you). The first great target is your email, which often allows for resetting a password using your phone number. With your email, they can find where your money is stored – Vanguard, Fidelity, Coinbase – wherever. They issue a password reset on these services – and since they have your email address and your phone number for 2-factor authorization, they are immediately granted access.
5. Take Over: With unlimited access, they can now start doing damage. They can log you out of all devices, change settings and passwords, change security questions and addresses. This makes it that much harder for you to prove ownership and retake the account – buying the thief time.
6. Transfer: If this is a financial account, the goal will be a heist – stealing your money. They liquidate what they can and transfer out the funds ASAP. If this is a social media account they want the handle of, they change the password and resell it to someone else.
If this sounds scary it’s because it is! It also happens all the time.
One of the best reports on this happening that I’ve heard about recently was an episode of the Reply All podcast called The Snapchat Thief. In this episode, the hosts of Reply All go on a journey into a den of thieves (which turn out to be all guys in their late teens or early 20s) who steal social media handles and resell them. It’s a really good episode if you’re curious to learn more.
The Cyber Podcast by Vice via Motherboard is another amazing one tackling this issue:
One minute, you’re using your phone as normal. The next minute, you lose cell service. “No SIM,” a message in the top left corner reads. You’re confused. You grab your computer, and try to login to your email. The password has been changed. Same with your Facebook. Your phone rings, apparently switched back on. On the other side is a hacker, who tells you that he’s stolen your phone number and your accounts, and that he’ll give them back if you send him Bitcoin.
Cyber Podcast episode “SIM Hijacking and the Phone Ransom”
Whether someone is stealing from your investments, your social media handle, or blackmailing you with photos you’ve saved to Snapchat, the attack vectors are often the same – and this means you can protect yourself if you know how.
How to Protect Yourself from the Dreaded SIM-Swap
We have tons of accounts and each one has a plethora of settings. Securing yourself requires taking a few steps. The more steps you take the better. At a high level, here’s what I’d recommend you do:
- Use different, long passwords for every service.
- Don’t use your phone number for anything you don’t want to lose.
- Switch to alternative 2-factor authentication methods.
- Turn security settings up to 11 on all important accounts.
Let’s go over these one by one.
1. Use different, long passwords for every service
This one shouldn’t need explaining. If you use the same password everywhere then you should make it a priority to change any accounts you wouldn’t want to lose tomorrow.
You don’t need to remember every single unique password either. You can use a service like LastPass or 1Password to store every one of your passwords for you and even generate new ones. These services will even alert you if an account is potentially compromised.
For example, 1Password keeps track of public data breeches and will let me know if a site has been compromised.
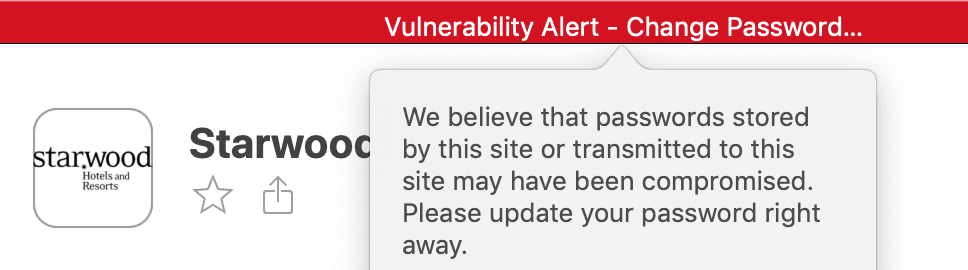
I might not jump to change my Starwood password, but if I saw my bank account here I’d change that in an instant!
At the end of this phase you should have strong, unique passwords for your most important websites.
2. Don’t use your phone number for anything you don’t want to lose
There is one key way to protect yourself from SIM-swapping: don’t use your actual phone number!
This may seem a little simple, but it’s an important step. Your phone number is easily findable. If you’ve ever been the victim of a data breach (chances are you have, but you can check on Have I Been Pwned), then your phone number is one of the easiest fields to get access to.
The trick to good security is to use a completely new number that you never share with anyone. You don’t need to buy a burner phone for this. Instead, you can get a free phone number through Google Voice or Skype. You’ll want to make sure that this phone number doesn’t forward calls or text to your primary number. That would defeat the purpose.
Keep this number secret and keep is safe. Only use it on your most important accounts. I think it’s a good idea to use this number for anything where you have money or the ability to make money from. If someone is going to SIM-Swap you, then they likely won’t bother with stealing your credit card info.
The one place that is tricky is your Google Account, which has a phone number in case of reset. If you’re locked out of your account, you should assume you’re locked out of your Google Voice account so you wouldn’t want to use that number here. Luckily you can remove this phone number and use an email address instead. I’d recommend setting up another (also secure) email address that you can access in case of an emergency.
At the end of this phase, you should have your Vanguard account, Fidelity, and wherever you have money using a new phone number that no one else knows about. Never share it with others or add it to your address book. If you’re using LastPass or 1Password, you could add it in there for safe storage and reference.
3. Switch to alternative 2-factor authentication methods
While you could rely on your new phone number for authorization, there are better options out there! Not every site supports them, but many do. For those that don’t, just use your new secret phone number. There are a few standards out there for 2fa that have become very popular and add another level of defense.
OTP (One time password) Auth – App Driven Passwords
This is one of the most common options out there. After you log in with your username and password, you open up some other app that generates a one-time use password (usually 6 numbers long) that you use to log in. Since this number changes every 30 seconds, even if someone had stolen your password, or had a keylogger on your computer, they wouldn’t be able to access your account. Google Authenticator and Authy are two popular OTP apps, but I prefer to use 1Password. LastPass also supports one time passwords.
Supported by: Google, Facebook, Twitter, Betterment
Not Supported by: An embarrassingly high number of financial investing companies.
WebAuthn, FIDO2, U2F – Hardware Driven Auth
Using OTPs, you’re required to have access to your username, password, and a one time password. With hardware driven auth you need to have access to your username, password, and an authorization device – usually plugged into your USB port.

I only recently learned about hardware auth options. They are incredibly easy to use – really! They work like this:
- You buy a hardware device. I’d recommend a YubiKey 5 Nano if you have old style USB ports, or a YubiKey 5C Nano if you have the newer USB-C ports.
- Plug it into your USB port on your laptop.
- Login to a site that supports it and go to “Add a key”.
- At some point, the webpage will ask you to “tap” your key. This will bring up a browser dialog asking if you want to allow Vanguard (or whatever the site you’re on) to use your key.
- Magic happens!
- The site has now connected your physical key to its website.
It’s really that easy. Take a look at this complicated graphic on Vanguards website explaining it:
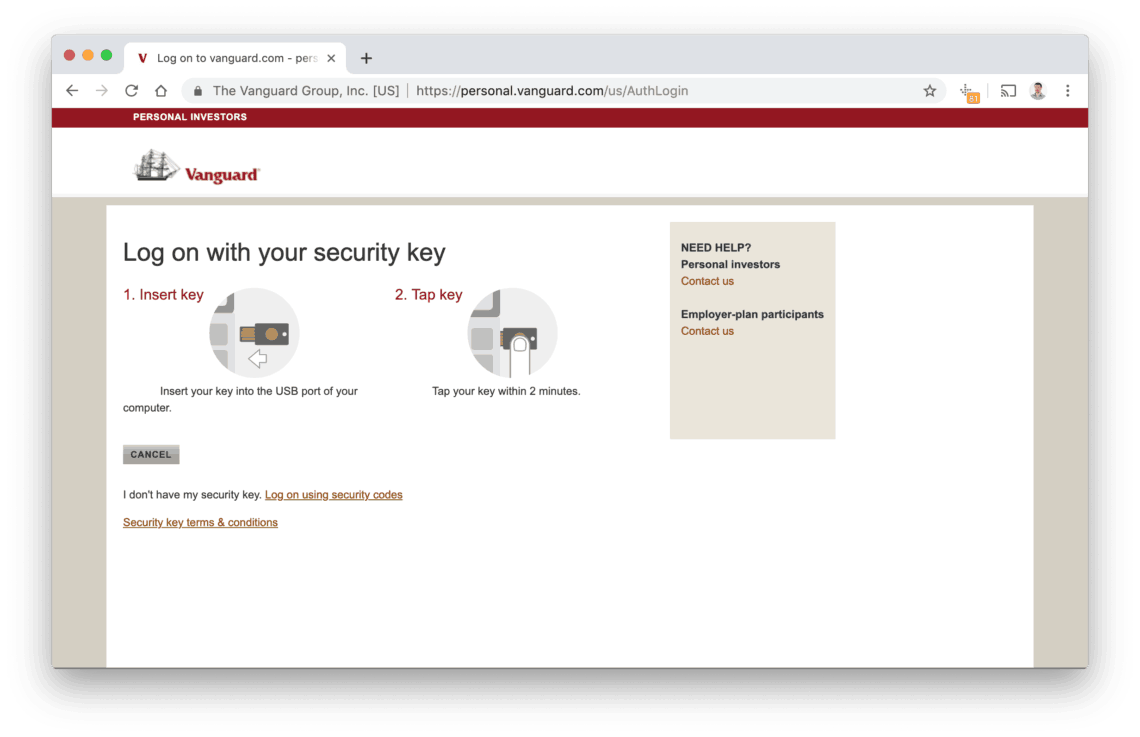
When I tap the key, it takes about a second or two, then the Vanguard screen advances to my dashboard. That’s it. It’s even easier than entering a one time password.
Reading more about YubiKeys online, one recommendation is to have 2-copies of your key (buy 2 hardware devices). That allows you a backup in case the first is lost. My key lives in my laptops USB port and goes wherever it goes. The only way I’d lose it is if I lost my entire laptop.
Another option if you’re in a relationship would be to have 2 keys – one for you and one for your partner. Most services allow you to register multiple devices – giving you a backup in case your primary ket is lost. The key alone doesn’t grant access to your account, but if you should lose your key, you’d still be able to get into your accounts with your password and their key (this is the route Mrs. Minafi and I are going).
Supported by: Google, Facebook, Vanguard, GitHub, 1Password, Dropbox, LastPass and a bunch more.
Not Supported by: Pretty much everyone else.
Custom 2-factor Authorization
A few sites offer a completely custom option for 2fa. You may have experienced these before. If you log into Facebook on your computer, it may ask you to open up your phone and verify it’s you. Google has an option to do the same – requiring you to open up the Gmail app and confirm a login from another device.
These options both do the job. If they know you’re you on your phone and you grant access to your computer, that’s a trusted recommendation. There is a potential problem with these where if someone is trying to hack you and receive a prompt, only to click “accept” when you should have clicked “reject”.
When in doubt I choose one of the other options over custom 2-fa, but if that’s the only option it’s better than nothing.
4. Turn security settings up to 11 on all important accounts.
Wow, you must really want to secure your stuff! Assuming you’ve created good, unique passwords, removed your phone number from everything you can think of, turned on 2-factor authorization you might be thinking – what else is there?
What’s left will be different for each site. I’ve been going through this process myself and have found some settings to be extra helpful:
Vanguard Security Settings
Sadly, even with 2-fa enabled, Vanguard will allow you to login on a mobile device with username and password. In order to disable this, you’ll want to login to Vanguard and go to “My Account” > “Account Maintenance” > “Computer access restrictions” and turn on “Restrict unrecognized computers, browsers, or mobile devices from accessing my accounts.“
What that’ll do is prevent anyone from accessing your account on an unrecognized computer or device. If you do get a new computer, you’ll want to disable this, login, then re-enable it. If you completely lose your computer you’ll need to call Vanguard and figure things out with them.
The downside is that this will completely prevent you from being able to use something like Personal Capital or Mint to track your investments since they’ll lose access. I prefer to sleep well knowing that my accounts are secure, and have since switched to manually tracking investments on these services.
Google Security Settings
Google’s security page has a TON of options. It took me a good hour to go through everything in there. There aren’t too many caveats, other than to make sure you public phone number isn’t on there as a recovery method or for 2-factor auth.
Google also asks you to setup a recovery email address – one that you can use if you lose your password on the Google Account. You’ll want to make sure you’re taking the same steps with that email account as you are with your primary account.
The last, and possibly most important thing to do is to generate backup codes for your main email address. With these are backup codes you can access your account using only email, password and the code – bypassing your YubiKey, or other 2-FA method.
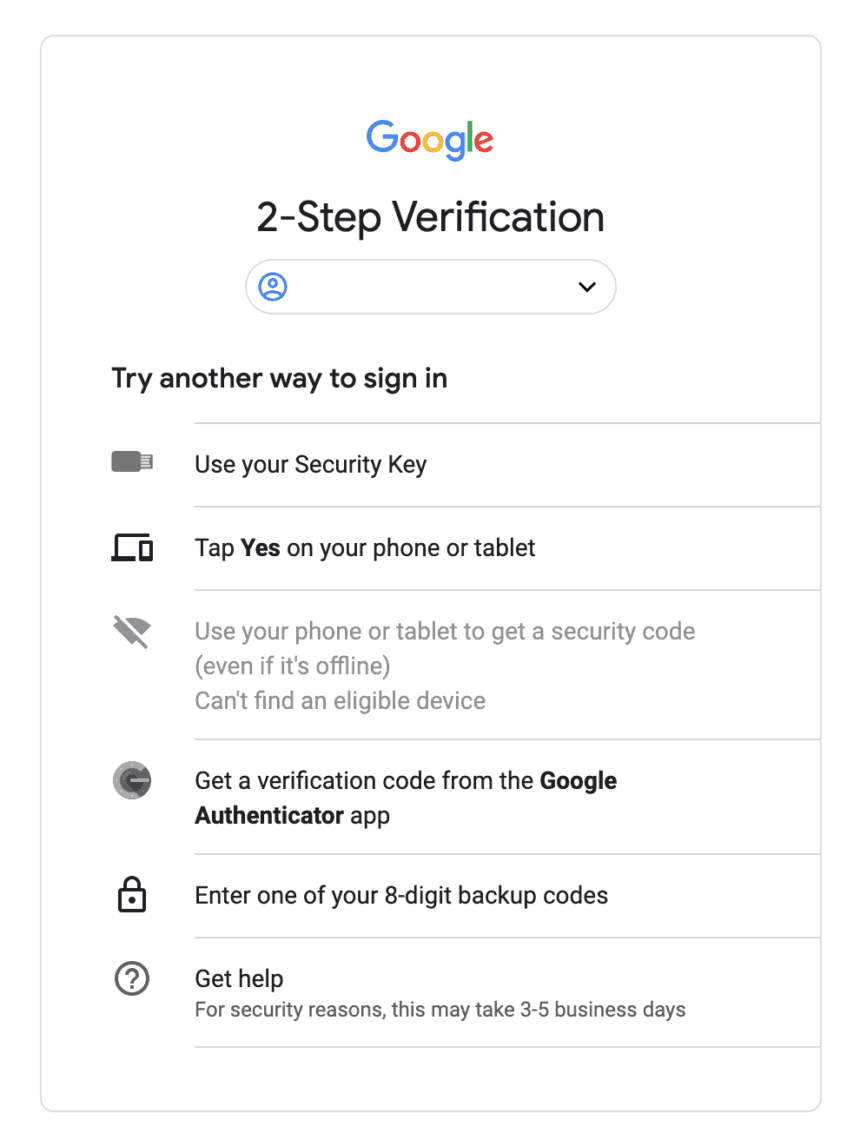
Print out these codes and store them in a safe place. I keep a copy with my last will and birth certificate as a “just in case”. Hopefully I’ll never need to use them, but they’re good to have. If you do need to, you can sign in and use one of your 8-digit backup codes here.
Get Chatty
Another setting to enable for any services you think are important is for them to alert you whenever anything happens. Someones trying to log in? Email you. Someone just changed a setting? Email you. Someone changed your phone number? Email you.
When you’re first setting up your line of defense you’ll get a ton of emails, but after that, they’ll quiet down. The concern would be that you become accustomed to these emails and ignore an important one. If you receive an email at a time when you’re not expecting it you may be able to find a security breach far before the damage is done.
Get Your Spouse on Board
If you have accounts with multiple people on them, that’s multiple ways someone could use to get in. If you and your partner both have access to your Vanguard account or your bank account, it’s important to go through this security audit for both of you. A thief only needs one unlocked door.
Set a PIN with your Cell Phone Carrier
This is one of the most simple things you can do, but it can thwart a thief in their tracks. Call your cell phone carrier and ask them to add a PIN number to your account to be used in the event of a number transfer. If a thief (or future you) calls to port your number to a new phone your carrier will ask for that PIN number before completing the transfer.
My carrier (Mint Mobile) uses PIN numbers but sadly gives them out to anyone who can answer a few questions about me. That’s the same for most carriers. The biggest vector for an attack is social engineering the gatekeeper at your phone company. Don’t rely on them to be watch guards for your most valuable accounts.
Protect Yourself – It’s Worth the Time!
It was only a week ago I made all of these changes, but since then I feel much more secure about my financials and accounts. Setting up a YubiKey 5 (the current model) was easy enough, as was moving to a Google Voice number.
I think this is extremely important to do, especially if you’re in the public eye in any way (a blogger, interact with the community, share anything on Twitter).
The idea of becoming a target of SIM-Swap may sound far fetched. I hope it never happens to me or to you. The important thing to do is take steps now so that if it does happen you’re not going to lose years (or decades) of work overnight.
SkunkFI
December 27, 2020
This is a great post. I recommend turning on Google Advanced Protection at https://g.co/advancedprotection to get Google’s strongest account security and really lock down your Google account and Google Voice number. It is too bad that some financial institutions, like TD Ameritrade, block using Google Voice numbers for 2FA.
allendave
August 6, 2024
Investment is one of the best ways to achieve financial freedom. For a beginner there are so many challenges you face. It’s hard to know how to get started. Trading on the Cryptocurrency market has really been a life changer for me. I almost gave up on crypto at some point not until saw a recommendation on Elon musk successfully success story and I got a proficient trader/broker Mr Bernie Doran , he gave me all the information required to succeed in trading. I made more profit than I could ever imagine. I’m not here to converse much but to share my testimony; I have made total returns of $10,500 from an investment of just $1000 within 1 week. Thanks to Mr Bernie I’m really grateful,I have been able to make a great returns trading with his signals and strategies .I urge anyone interested in INVESTMENT to take bold step in investing in the Cryptocurrency Market, he can also help you recover your lost funds, you can reach him on WhatsApp : +1(424) 285-0682 or his Gmail : [email protected] tell him I referred you
Joe Hill
March 2, 2021
Really an excellent article, it covers everything. Well done!
Adam
March 2, 2021
Thanks Joe!